In today’s digital age, data breaches and incidents involving personal information have become a significant concern for businesses and individuals alike. With the implementation of the General Data Protection Regulation (GDPR), companies handling personal data are required to take strict measures to protect that data and respond effectively in the event of a breach. Having a solid step-by-step plan and a software solution in place is crucial for surviving GDPR data incidents and mitigating their impact. In this article, we will explore the importance of such a plan and how to ensure a swift and effective response.
1. Why does it matter?
Data incidents, such as data breaches or unauthorized access to personal information, can have severe consequences for organizations. GDPR, implemented in 2018, aims to protect the privacy and security of individuals’ personal data within the European Union. To survive GDPR data incidents, organizations must be prepared with a comprehensive response plan.
2. What is a GDPR Data Incident?
A GDPR data incident refers to any breach or potential breach of personal data that falls under the scope of the GDPR. This includes unauthorized access, loss, alteration, or destruction of personal data. GDPR defines personal data as any information relating to an identified or identifiable natural person.
Here are some obvious examples of data breaches:
- Insider Threat: An employee with authorized access to sensitive customer data intentionally or unintentionally leaks confidential information to unauthorized individuals or external entities. The breach compromises the privacy and security of customer data, leading to potential identity theft, fraud, and reputational damage for the organization.
- Phishing Attack: Cybercriminals launch a targeted phishing campaign, tricking employees into revealing their login credentials or other sensitive information. With unauthorized access to employee accounts, the attackers gain entry into the organization’s systems, compromising customer data, intellectual property, and potentially conducting further malicious activities.
- Ransomware Attack: A sophisticated ransomware attack infiltrates an organization’s network, encrypting critical data and demanding a ransom for its release. The breach disrupts business operations, compromises customer data, and may result in financial losses and reputational harm if the organization chooses not to pay the ransom.
- Mobile Device Theft: A mobile device containing sensitive customer information, such as smartphones or laptops, is stolen or lost. If the device is not properly encrypted or protected with strong security measures, the data becomes vulnerable to unauthorized access, potentially leading to identity theft, data misuse, and financial fraud.
- Third-Party Data Breach: A vendor or business partner with access to an organization’s systems or customer data experiences a data breach. The incident exposes the shared data, impacting both the organization and its customers. This breach underscores the importance of conducting thorough due diligence when engaging with third-party providers and ensuring strong data protection measures are in place.
You may be surprised to understand that these also are considered data breaches under the GDPR:
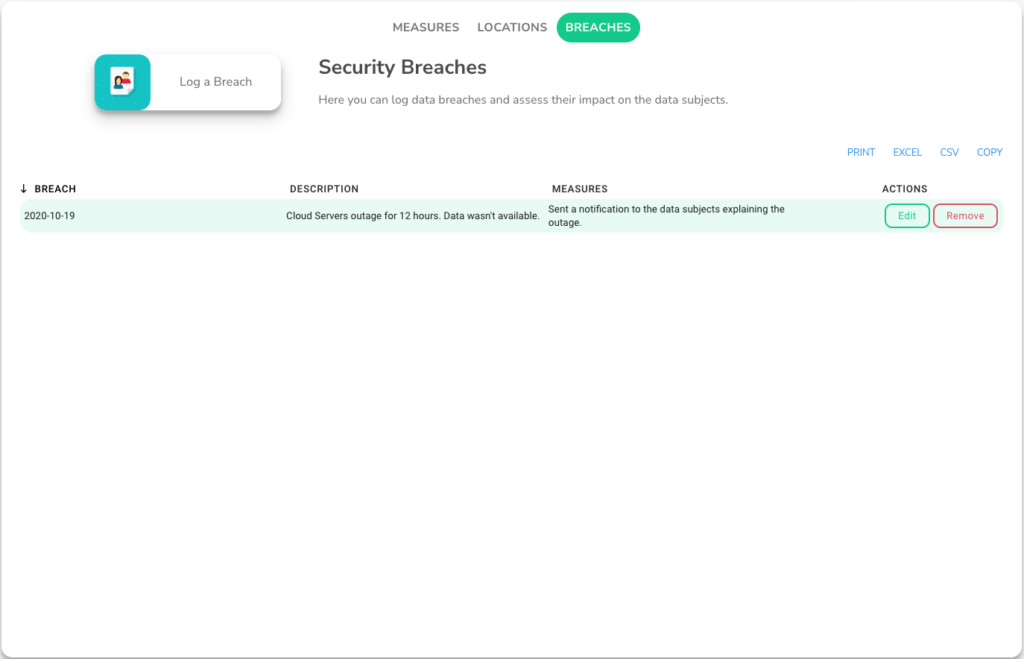
- outage of your cloud service provider (even when no data is lost or compromised)
- adding the wrong people in an email correspondence
3. The Importance of Having a Step-by-Step Plan
Having a step-by-step plan for responding to GDPR data incidents is crucial for several reasons. Firstly, it helps organizations maintain a systematic and organized approach during a highly stressful and time-sensitive situation. Secondly, it ensures that all necessary steps are taken promptly, minimizing the potential damage caused by the incident. Additionally, a well-documented plan can serve as a valuable resource for training and educating employees on their roles and responsibilities in incident response.
To ensure a smooth and coordinated response to GDPR data incidents, it is essential to establish pre-defined responsibilities within the incident response team. Each team member should have clear roles and tasks assigned to them based on their expertise and responsibilities. Additionally, designating a person in charge of the action plan provides a central point of contact and accountability during the incident response process.
4. Key Elements of an Effective Response Plan
Acting swiftly and making the right decisions under pressure is crucial to handle the data incident. That is why automating the process as much as possible is key to a successful data breach response. A comprehensive response plan consists of the following key elements:
4.1. Incident Identification
The first step is to identify and assess the incident. This involves promptly detecting and confirming the breach, evaluating the potential risks and impacts, and determining the scope of the incident.
If you are processing a large amount of data you may consider implementing robust monitoring systems and employing anomaly detection techniques to identify potential data incidents in real-time.
Relying solely on manual detection methods may result in delayed identification of incidents, allowing them to escalate and cause greater harm.
Once the incident is identified the response plan is triggered. You shall designate a person responsible to manage the whole process.
4.2. Notification and Communication
Once the incident is confirmed, you must assess the risks of the data breach and decide whether to notify the supervisory authority and/or the data subject.
To correctly do that under pressure, it’s best to use ready-made templates or a software solution that will navigate you through the whole assessment process.
Notification to the supervisory authority
Notification to the supervisory authority is required when the breach is likely to result in a risk to the rights and freedoms of natural persons. In general, the notification must be done within 72 hours, unless you need more time to assess the breach. In that case, you will need to provide an explanation on why you decided to delay the notification to the supervisory authority.
Notification to the data subject
You are required to notify the data subjects only when there is a high risk to their rights and freedoms. However, you may consider notifying them nonetheless.
If the data was encrypted and the encryption key is not compromised, you are not legally required to notify the data subject.
Prepare template notifications in advance or use compliance software to ensure clear and consistent communication with regulatory authorities and affected individuals.
Composing notifications from scratch during a high-stress incident can lead to errors, inconsistent information, and potential non-compliance with notification requirements.
4.3. Data Breach Containment and Eradication
Efforts should be focused on containing the breach and preventing further unauthorized access to personal data. Steps may include isolating affected systems, applying patches and updates, and strengthening security measures.
Using a compliance software solution can greatly facilitate the delegation of tasks within the team. It can provide a centralized platform where team members can access the incident response plan and view their assigned tasks. The designated person in charge can use the software to assign specific actions to team members, set deadlines, and track the progress of each task.
4.4. Investigation and Remediation
Conducting a thorough investigation helps determine the root cause of the incident and identify vulnerabilities in existing systems and processes. Remediation actions should be implemented to address the identified issues and prevent similar incidents in the future.
Focusing solely on immediate remediation without understanding the root cause may result in similar incidents recurring in the future. Remember, trust is built slowly, but can be lost pretty quickly.
It is very important to document all investigation findings, including the steps taken, evidence collected, and lessons learned, to enhance future incident response capabilities. Neglecting to document investigation details can lead to a loss of valuable insights and prevent the organization from learning from past incidents.
Using a software solution can generate reports and provide visibility into the overall status of the incident response efforts. This allows the designated person in charge to have an overview of the tasks being performed, identify bottlenecks or delays, and make informed decisions to optimize the response process.
5. Conclusion
Surviving GDPR data incidents requires a proactive and well-prepared approach. Having a step-by-step playbook and a software solution in place significantly improves an organization’s ability to respond effectively and mitigate the potential damage caused by such incidents. By promptly identifying and assessing the incident, communicating transparently, containing the breach, conducting thorough investigations, and learning from the experience, organizations can enhance their data protection practices and build trust with their customers.
FAQs
1. What is GDPR? GDPR stands for General Data Protection Regulation. It is a regulation that aims to protect the privacy and security of personal data within the European Union.
2. Who needs to comply with GDPR? Any organization that handles personal data of individuals within the European Union, regardless of its location, needs to comply with GDPR.
3. Why is having a step-by-step plan important in GDPR incident response? A step-by-step plan ensures a systematic and organized approach during a data incident, helping organizations respond effectively and minimize potential damage.
4. How can software solutions assist in GDPR incident response? Software solutions can automate various aspects of incident response, including incident detection, communication, collaboration, and data breach analysis.
5. How should organizations choose the right software solution for GDPR incident response?
Organizations should consider their specific needs and requirements, such as incident tracking, workflow automation, and compliance with privacy regulations when selecting a software solution.
Start a free trial with Conformally: link
In conclusion, surviving GDPR data incidents requires a comprehensive step-by-step plan and the implementation of a suitable software solution. By prioritizing incident identification and assessment, effective communication, breach containment, thorough investigation, and continuous improvement, organizations can strengthen their response capabilities and safeguard the personal data entrusted to them.

